Building a Zero-Trust Infrastructure on Azure
Summarize with:
Zero Trust is a security strategy. It is not a product or a service, but an approach in designing and implementing security principles like Verify explicitly, using least privileged access, assume breach. Implementing Zero Trust in the cloud helps to “assume breach, never trust, always verify” and it requires changes to cloud resources and their deployment strategy.
Let’s get into the Zero Trust strategy in this blog!
Table of Contents:
Zero Trust Approach to Azure Services
Zero Trust Principles to Azure Storage
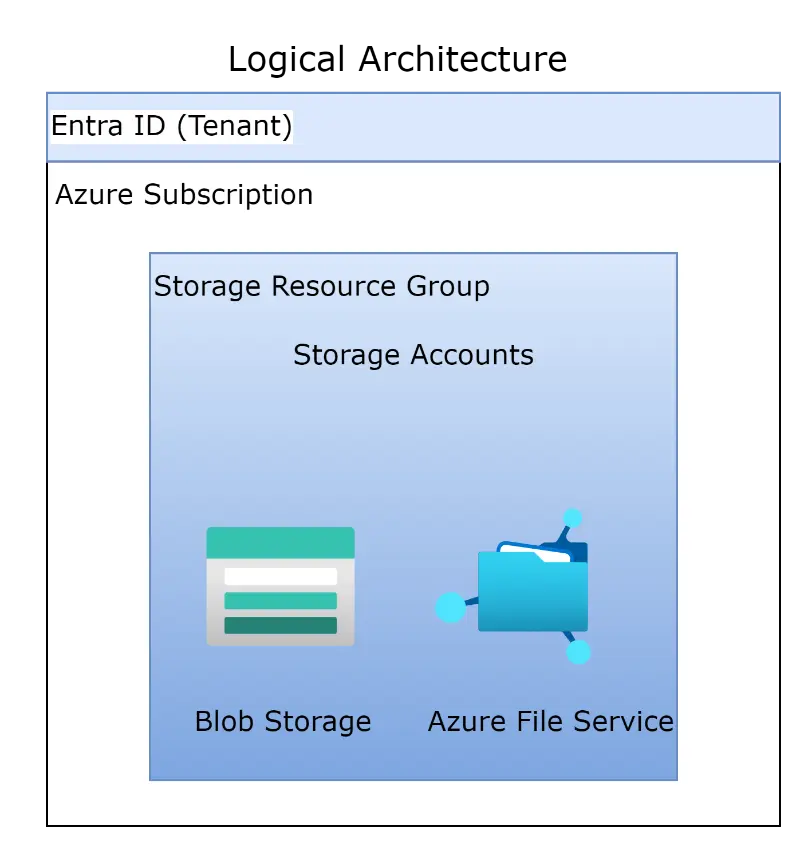
Microsoft Entra ID helps to govern access to storage accounts. Microsoft Entra ID is a more secure choice as you can use risk-based access mechanisms to harden the access. For more granular control use role-based access controls and isolate each storage account in a different resource group. In the case of multiple applications or workloads with multiple storage accounts in one Azure subscription, limiting each storage account’s RBAC permissions is important. Prefer using HTTPS to secure communication over public internet traffic.
Configure data protection for all three modes from the configuration settings of a storage account. Implement a minimum required version of transport layer security, this will reject requests from clients using older versions. Limiting copy operations to source storage accounts with private endpoints is the most secure option. Prevent public access and create network segmentation with Private Endpoint and Private Link. Use Service Endpoints to secure access to your confidential data. Use Defender for Storage for automated threat detection and protection.
Also Read: Speed Up Data Ingestion Using Azure Data Factory
Zero Trust Principles to Virtual Machines in Azure
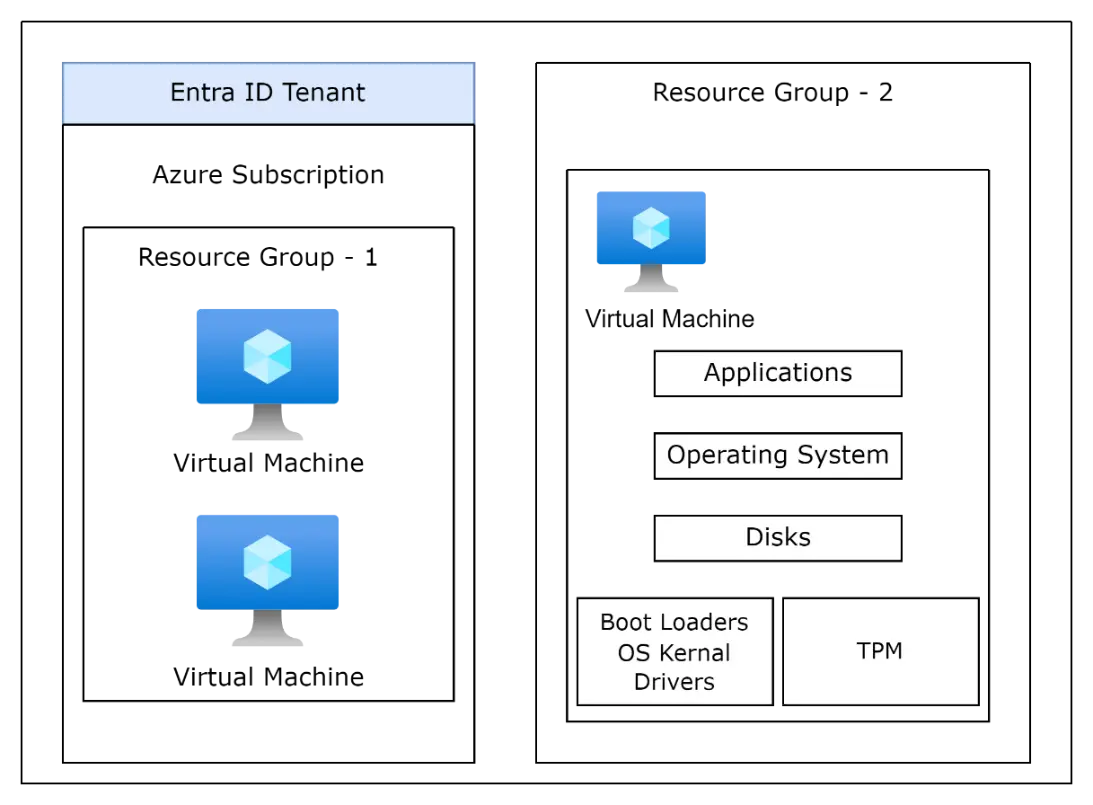
- Configure logical isolation by deploying virtual machines to a dedicated resource group.
- Use role-based access control to create the least privileged access.
- Enable just-in-time and just-enough access (JIT/JEA) based on the user role. Enable Secure boot, enable TPM, and Enable Integrity Monitoring.
- Enable customer-managed keys and double encryption, so that if a disk is exported, it is not readable.
- Implement Azure Bastion to secure connections to virtual machines.
- Enable System Assigned Managed Identity, this will allow Microsoft Entra tenant with Microsoft Intelligent Security Graph to support secure access.
- Enable the Virtual Machine Applications feature to control the applications installed on virtual machines.
- Set up multifactor authentication with conditional access, use privileged access workstations (PAWs), Secure maintenance of virtual machines, use anti-malware, and automate virtual machine updates.
- Enable Microsoft Defender for Cloud, this protection is extended to virtual machines when you deploy it.
Zero Trust Principles to a Spoke Virtual Network in Azure
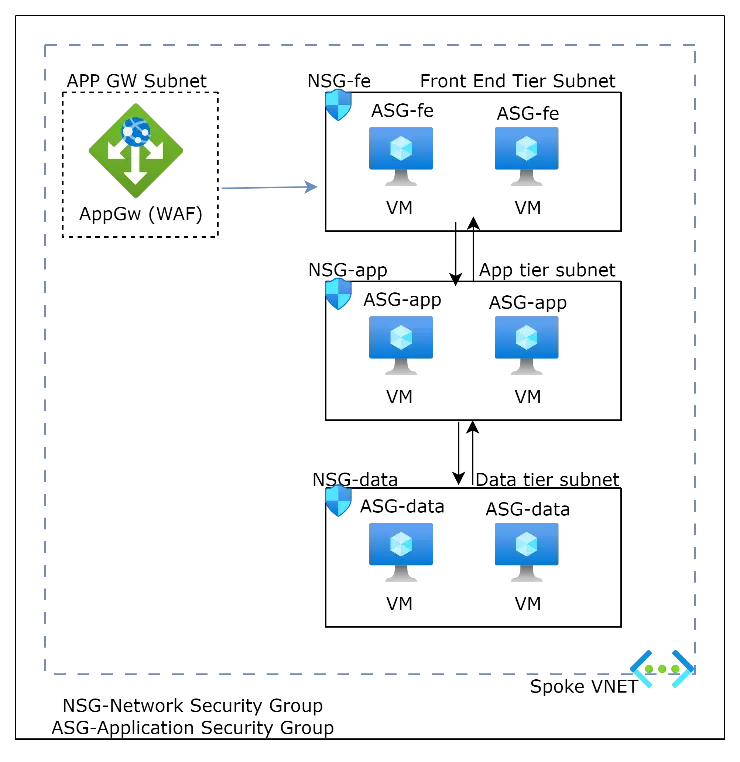
- Use Microsoft Entra role-based access control (RBAC) or set up custom roles for networking resources. Isolating network resources from computing, data, or storage resources can reduce the possibility of permission aches.
- Preferably having the spoke network resources available in multiple environments in a shared resource group, creates a dedicated resource group.
- For a multi-tier virtual-machine-based application, creating a dedicated network security group for each subnet that hosts a virtual machine role is recommended.
- Implement baseline deny rules for network security groups to enforce the least level of access. Create an application security group for each virtual machine role.
- For each traffic pattern, create a rule explicitly allowing it and you should do so with the least permissions.
- Plan for management traffic, use multi-factor authentication and conditional access policies for users to access the application. Enable Microsoft Defender for advanced threat detection and protection.
Zero Trust Principles to a Hub Virtual Network in Azure
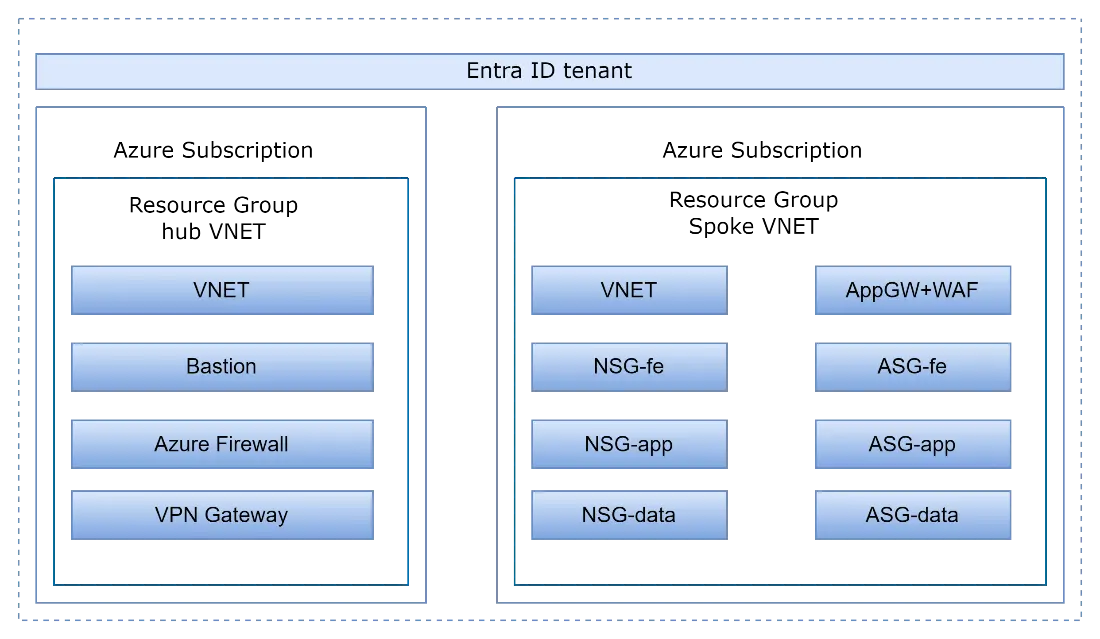
Azure Firewall must be secured using a premium license so that we can apply the zero trust principle to a hub virtual network. Deployment of network gateway routing to the firewall along with enabling DDoS protection standards required.
Azure Firewall Premium is powerful in helping you secure your Azure infrastructure for Zero Trust. Implement route tables on various subnets to ensure the Azure Firewall inspects traffic between spoke VNETs and the on-premises networks.
Deploy the Azure Network Gateway in the hub VNETs, configure routing on the gateway subnet, and then configure routing on the spoke VNETs subnets. Implement spoke subnet routing and ensure the route table is attached to your spoke VNET subnets, with a default route to forward traffic to the Azure Firewall. Configure threat protection, Microsoft Defender for Cloud can protect your hub VNETs built on Azure.
Zero Trust Principles to an Azure Virtual WAN
Azure Virtual WAN is a networking service that brings networking, security, and routing functionalities. Azure Virtual WAN is a collection of hubs and services made available inside a hub. Azure Virtual WAN provides some traffic encryption capabilities, encryption should be enabled, based on the gateway type. Deploy Azure Firewall or supported Next Generation Firewall (NGFW) NVAs inside each Virtual WAN hub. Implement inter-VNET and on-premises branch routing by sending all traffic to security appliances in the hubs for inspection. The resources in the spokes should not have direct access to the Internet. Implement monitoring, auditing, and management for Azure virtual WAN.
Why Zero-Trust
Implementing the Zero-Trust approach reduces the risk of unauthorized access and data breaches. Zero Trust helps mitigate the risk of insider threats. Minimize the overall organization’s attack surface. Zero Trust helps organizations meet compliance requirements, like GDPR, HIPAA, etc. Zero Trust improves business continuity by decreasing the impact of security incidents.
Industry Trends
Most of the organizations leading in digital payment markets are adopting Zero-trust principles.
By applying the Zero-Trust principles organizations improved their productivity more than expected. The business enterprises adopted a Zero-trust principle, allowing real-time response from a dynamic security architecture. Businesses that implement the zero-trust principles can mitigate risks and maintain regulatory compliance.
Check out EXCLUSIVE: Hurix Digital Secured 99.9% Uptime for a $800M Retail Giant Using Azure Disaster-Recovery Solution
Conclusion
Leveraging the Zero Trust principles strengthens the security posture of organizations. it is a proactive approach to cybersecurity that prioritizes continuous verification and strict access controls. The security of an organization’s resources like identity, endpoints, networks, applications, and data on Azure Cloud.
Visit Hurix Digital’s Cloud Services to get a smooth cloud adoption journey.
Summarize with:

Vice President and Strategic Business Unit Head – Cloud Services
A top technology management voice on LinkedIn with 20 Years of experience in Information Technology, Cloud Services, Digital Transformation, Application Modernization, Managed Services, IT Security Engineering and Operations Management. An avid technology Leader, Leadership Speaker, Author & Coach.
 A Space for Thoughtful
A Space for Thoughtful